Development
Why Choose a Bespoke WordPress Theme Over a Template?
Discover why choosing a bespoke WordPress theme over a template can boost performance, SEO, and flexibility for your growing business.
20th April, 2025
Since it was established in 2003, WordPress has continued to grow its user base and market share at an extraordinary rate due to its ease of use and incredible functionality. In fact, it now powers over a third of all websites which is no small feat considering its extremely humble beginnings.
Today, tomorrow, next week or next decade; WordPress is and will be the ideal platform to found your online venture, the amount of flexibility afforded to developers and marketers alike is truly remarkable. It’s easy to develop, easy to add content, easy to change the aesthetic and SEO ready. WordPress is unique in its ability to be flexible and adaptable to changing requirements, as the internet evolves so does WordPress.
This popularity however does come at a cost by painting a huge target on the back of webmasters across the globe. Whilst WordPress is the foremost content management system available on the market today due to its ability to do virtually everything that you would want from a website, steps MUST be taken to prevent your WordPress website from being hacked. As the old saying goes: “prevention is better than cure”, and the same is true when it comes to hackers trying to gain access to your website. Once they have gained access, it can be extremely problematic removing them and their Trojan horses.
The open-source nature of WordPress, a large part of the reason it’s so popular, is the very same reason learning how to exploit holes in its security is incredibly realisable to those wishing to cash in on unsuspecting WordPress webmasters.
Too many plugins?
The main culprits for these exploits come from the catalogue of over 50,000 third-party plugins designed to aid user experience and cater to the webmaster’s specific needs.
Wordfence, one of the foremost web application firewalls (WAF) recommends using as few plugins as you possibly can. The more plugins you install, the more advanced functionality you introduce to the website, but this is a two-way street as the more plugins you have enabled, the more potential backdoors to your website you’ve just willingly introduced.
To clarify, neither WordPress nor its plugins are inherently insecure or vulnerable to hackers, it’s the sheer volume of sites using this platform that creates a vulnerability. There are currently more than 1,752,326,743 websites on the internet, and with WordPress currently holding 35% market share, that’s 613,314,360 WordPress websites and counting which paints a large target on your back as the hackers trying to access websites have a greater pool of ‘doors to knock on’, as it were. It makes more sense for them to spend time writing one script that can potentially infiltrate 613,314,360 websites than to create one that infiltrates the TYPO3 CMS platform that holds just a 0.0001% market share with 285,281 live websites.
A WordPress website, or any other website for that matter, that has been infiltrated by a hacker can cause devastation to your online business and even deteriorate the trust loyal followers of your business have in your brand, as hackers can steal sensitive information: email addresses, passwords, phone numbers and even physical addresses.
Breaking in through the backdoor…
If that alone did not cause concern, more often than not the clever hacker will place a backdoor into your website, making it much easier to regain access to your website in the future. “Backdoors” are simply re-entry points that allow the hacker to maintain their access to the website, and these backdoors come in many shapes and sizes. Some hackers will simply create a new administrative user, whereas others will generate scripts and hide them in the tens of thousands of lines of code that make up your website, ensuring they’ll maintain control of, and access to the website for as long as it takes for someone to discover their unscrupulous deed.
These scripts can install all manner of nasty traps onto your website that unsuspecting users can fall into, such as malware and phishing elements. Also, if they’re constantly being implored to fill in their credit card details to receive *100 FREE EMOJIS* as a direct result of visiting your website, you’re likely to lose brand loyalty forever.
Moreover, Google blacklists upwards of 70,000 websites for phishing and malware every single week which would put an abrupt halt to you receiving visitors and thus revenue.
Hacked websites are the bane of every website owner’s existence and for good cause, so how exactly do you go about defending your website and business from hordes of anonymous people from around the globe?
Defending your WordPress installation: KEEP EVERYTHING UPDATED!
98% of hackers successfully gained access to the website via third party plugins according to an Imperva study and judging by this ever-expanding list, that isn’t a statistic likely to change any time soon.
SQL Injections, Malware and Cross-Site Scripting are just a few reasons to keep your WordPress core updated along with ensuring your WordPress plugins are all updated and currently supported. According to WordPress security plugin developers, Sucuri, 44% of hacked websites were a result of an outdated and insecure version of WordPress.
It’s not just your plugins at-risk either, outdated WordPress themes can be equally troublesome to webmasters.
Plugins and WordPress updates can be managed in house, or you if this is not your area of expertise it may be a good idea to engage a developer/digital agency to look after the security of your site on a regular basis. First Internet has a number of SLAs in operation for its clients to ensure their WordPress installation and plugins are looked after on a regular basis. If you’d like us to look after this on your behalf, just give us a call on 0161 941 5330.
Is your WordPress theme ‘cracked’?
Another route in for hackers may be your choice of theme. Downloading, ‘cracked’ WordPress themes from torrenting websites is a sure-fire way to compromise your WordPress website – what’s more, you’re not supporting the developer’s efforts in creating the theme. Always download WordPress themes from reputable suppliers such as Theme Forest or MyThemeShop to avoid having rogue lines of code allowing hackers access to crucial areas of the website such as wp-login.php.
Sometimes, however, the theme creator simply stops supporting their theme. Whilst there are tools to help you establish whether an outdated theme is compatible with your WordPress build, you should focus on looking for a new, updated theme as soon as possible. As elements of the older theme begin to fail, potential vulnerabilities will crop up and hackers will start looking closely at your website.
Alternatively, if you have a dedicated WordPress developer they will be able to check the inner workings of the outdated theme and make amends, if necessary, to fall in line with newer WordPress core versions.
Brute Force Attacks
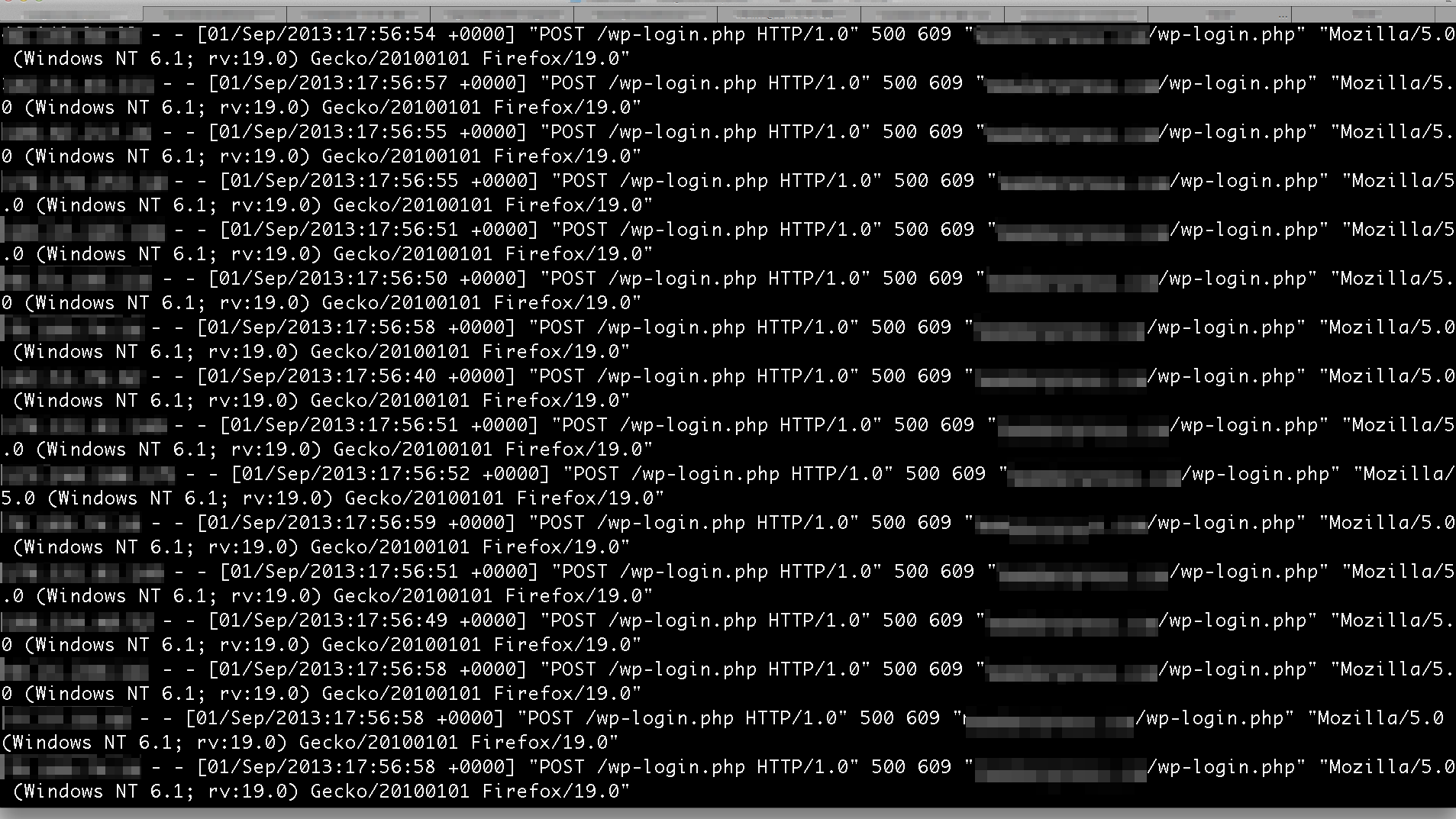
As well as vulnerabilities caused by plugins and cracked themes, you could be at risk of a brute force attack. A ‘Brute Force Attack’ is a method of gaining access to your WordPress installation by using a database of username and passwords that are systematically tried until the correct combination has been found, allowing the hacker access to the backend of your website. Hackers do this by simply running a program which exhausts every possible combination of username and password and leave it running for as long as it takes to gain entry. These programs also wreak havoc your websites available bandwidth, expect websites that are being brute forced to slow to a crawl.
These dictionaries can contain billions of passwords everything from the generic “password” to combinations most people would consider more secure. This one, in particular, is responsible for cracking approximately 30% of website login credentials.
When the WordPress hacker can easily set one of these programs up to systematically try and infiltrate your business and then go about their day, it’s definitely worth taking steps to thwart their efforts. You can do this by updating your password for your “Admin” WordPress users, and whilst you’re at it, change the username from admin to something, anything else – WordPress installations as standard come with the Admin as the generic, all-powerful, webmaster login. So as a standard, that username is one of the first things the hacker will attempt to log in with.
Another step you can take is to change the login URL to something completely random instead of examplewebsite.com/wp-admin or examplewebsite.com/wp-login.
Has Your WordPress Website Been Hacked?
Even the most dedicated of webmasters can’t monitor their websites on a constant basis, and as any hacker worth their salt will take several steps to conceal their actions, it may not always be obvious at first.
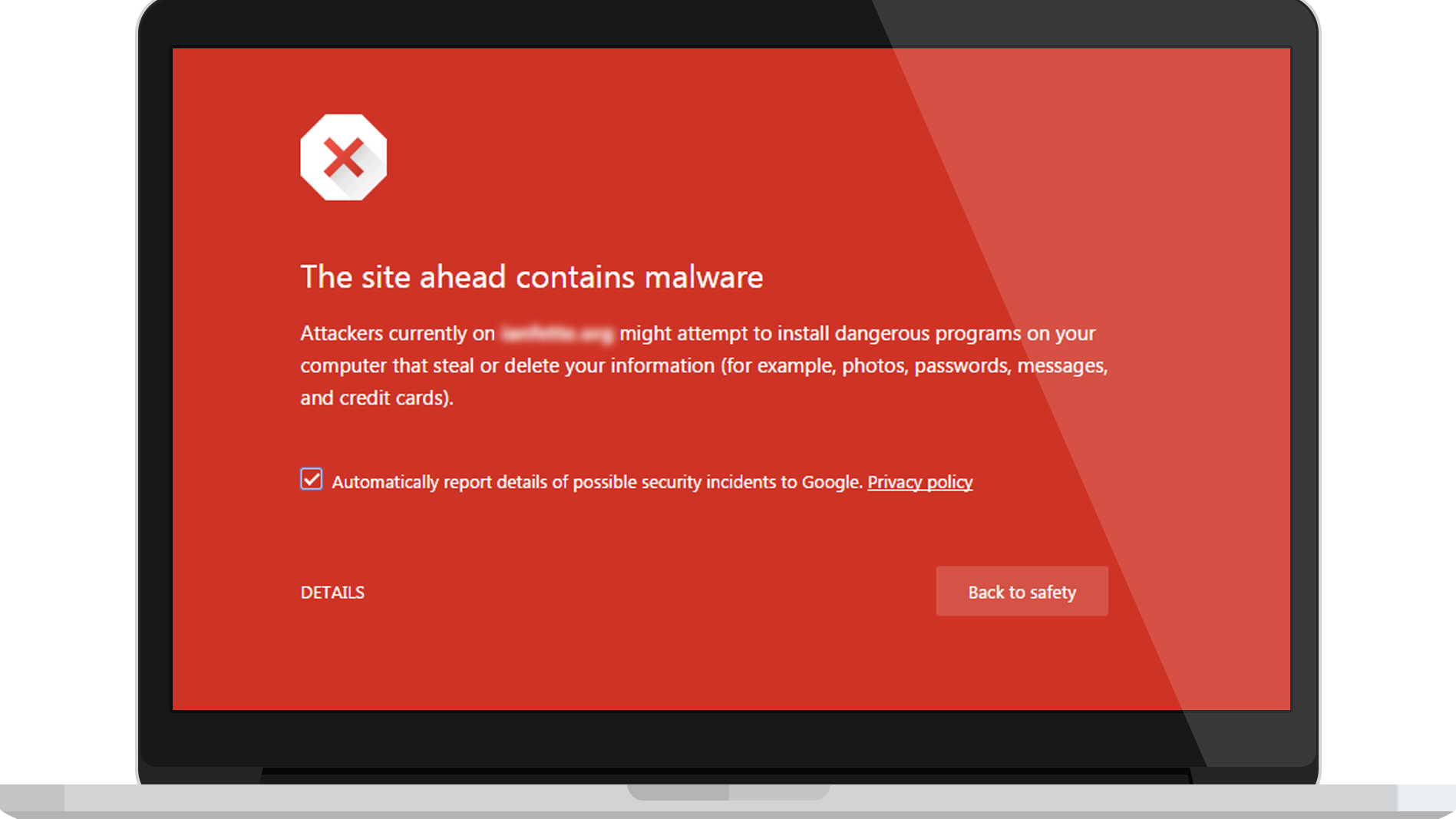
There are, however, a number of things that might alert you to inconsistencies in your website security. Google Chrome and Search Console will both flag a compromised website and Google will even make you aware that the website is compromised within the search listings.
But at that stage, it is often already too late, the hackers have not only infiltrated the website but taken steps to assure that they can regain entry should the website be ‘cleaned’ of infection. At that stage it’s better to call in the professional developers to get to the root of the problem and stem the loss of earnings and rankings caused by the malware present on the website.
If you think that your WordPress website may have been compromised or you’re worried about this happening in the future, act now and get in touch with our team today.
Development
9th March, 2020
Call us on: +44 (0) 161 941 5330 or email us: info@firstinternet.co.uk
Get in touch today!